LIST THE RECOMMENDED STEPS IN DIGITAL FORENSIC INVESTIGATION
Evenings On Campus or 100 Online. Analyze Identify the type of attack define its scope determine the data exposed or stolen and the potential impact of the.
Introduction Of Computer Forensics Geeksforgeeks
Ad AMU offers 200 online degrees and certificates- both undergraduate and graduate programs.
. Stage of an investigation or prosecution. Carroll Director Cybercrime Lab. Ad EDT- 40 years of providing unbiased technical answers for engineering litigation matters.
There are four phases involved in the initial handling of digital evidence. In the case of Secure Cyber Defense we have a three steps process. Technology is advancing at.
But in the way you handle things remember to reach out and use your resources as you go through this process. Capturing the data Any work carried out on data should be on copies only always preserving the integrity of the original data. Consulting Engineers Nationwide - Let us match your needs with an engineer today.
Ad AMU offers 200 online degrees and certificates- both undergraduate and graduate programs. Evenings On Campus or 100 Online. Consulting Engineers Nationwide - Let us match your needs with an engineer today.
Chief of Computer Forensics and Investigations US. Creating a digital evidence forensic unit. See Cybercrime Module 4 on Introduction to.
Identification collection acquisition and preservation ISOIEC 27037. In order for digital evidence to be accepted in a court of law it must be handled in a very specific way so that there is no opportunity for cyber criminals to tamper with the evidence. Method as a baseline for formulating digital forensic validations.
The framework introduces two key properties. Gather human intelligence Plan your approach Obtain evidence Analyse the evidence Report on your findings You can find detail description of the steps in the article. Pulling data off the drives and such.
Recognize identify seize and secure all digital evidence at the scene. The guide could be used within cybersecurity firms cyber incident response teams CIRT or within other organizations whereby cyber forensics investigations. Learn from practicing experts and earn your degree in Criminal Justice.
Ad EDT- 40 years of providing unbiased technical answers for engineering litigation matters. Ad Learn How to Conduct a Digital Crime Scene Investigation. Study Part-Time or Full-Time.
Ad Learn How to Conduct a Digital Crime Scene Investigation. Keeping a strong chain of custody ensures that the. It is recommended that forensic examiners follow these four basic steps as a starting point for an internal validation program.
The process is potentially iterative so they also. Study Part-Time or Full-Time. Learn from practicing experts and earn your degree in Criminal Justice.
So part of that of course is if you have. The most common steps performed in computer forensics investigation include search and seizure acquisition analysis and reporting. The first is identification and comprises event or crime detection resolving signature anomalous detection system monitoring audit analysis etc.
The rest of the paper. Follow the steps listed below to guide their handling of digital evidence at an electronic crime scene. Preparation phase Physical Forensics and Investigation phase Digital Forensics phase Reporting and Presentation phase and Closure phase.
Computer Forensics Lab and. Digital Forensic Analysis Methodology Ovie L. First the framework proposes a digital artifacts categorization and mapping to the generalized steps of attacks - Cyber-Kill.
Army Criminal Investigation Laboratory Forest Park Georgia.
Why Is Digital Forensics Important Packetlabs
Main Branches Of Digital Forensics Download Scientific Diagram
What Is Digital Forensics Types Of Digital Computer Forensics
Digital Forensics In Information Security Geeksforgeeks
Digital Forensics Investigation Steps By Yash Gorasiya Cyversity Medium
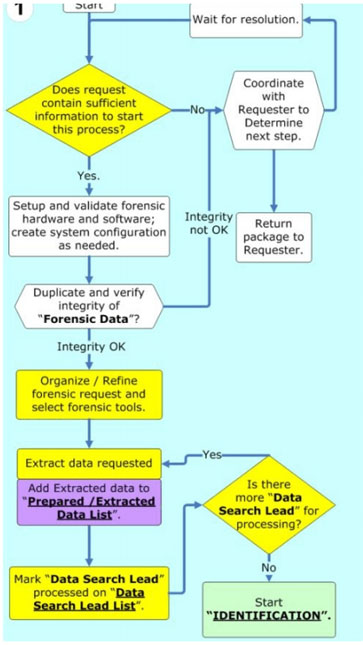
Computer Forensics Digital Forensic Analysis Methodology
Phases Of Cyber Forensics Download Scientific Diagram

0 Response to "LIST THE RECOMMENDED STEPS IN DIGITAL FORENSIC INVESTIGATION"
Post a Comment